Inlining
On-the-fly Inlining of Dynamic Dependency Monitors for Secure Information Flow
Luciano Bello and Eduardo Bonelli
Information flow analysis (IFA) in the setting of programming languages is steadily veering towards the adoption of dynamic techniques. This is particularly attractive for scripting languages for web applications programming. A common manifestation of dynamic techniques is that of run-time monitors, which should block program execution in the presence of an insecure run. Significant efforts are still required before practical, scalable monitors for secure IFA of industrial scale languages such as JavaScript can be achieved. Such monitors ideally should compensate for the absence of the traces they do not track, should not require modifications of the VM and should provide a fair compromise between security and usability among other things. This paper discusses on-the-fly inlining of monitors that track dependencies as a prospective candidate.
- On-the-fly Inlining of Dynamic Dependency Monitors for Secure Information Flow (Extended Version), Luciano Bello and Eduardo Bonelli. Proceedings of the 7th Workshop on Programming Languages and Analysis for Security ACM New York, NY, USA, 2012
- A prototype for a Python subset.
Instructions
Download and unpack the tar file with the prototype.
wget http://www.cse.chalmers.se/~bello/inlining/inlining_prototype.tar.gz tar zxvf inlining_prototype.tar.gz
Run the test files with different secrets. For example:
$ secret=0 python test00.py //OUTPUT: False $ secret=1 python test00.py //OUTPUT: True
Run the inlined version of test files with different secrets. The leak is detected in the second run. For example:
$ ./inliner_dep.py test00.py | secret=0 python //OUTPUT: False $ ./inliner_dep.py test00.py | secret=1 python //ERROR
For saving the inlined version:
$ ./inliner_dep.py test00.py > test00_inlined.py $ cat test00_inlined.py ...
The kappa.DB file stores the kappa states. If you want to forget the history, remove this file. It is possible to graph the dependency tree:
./inliner_dep.py -d test03.py | secret=2 python | dot -Tpng >deps.png ; display deps.png
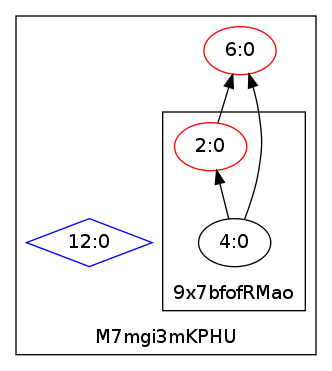
The boxes with the hashed are the contexts. Exec creates a new context.